| VaultPasswordView v1.10 Copyright (c) 2016 - 2020 Nir Sofer |
See Also
Description
This is how to hack windows with a Sam file. It will take some time, but it is the real hack. Well, to do this you have to have a basic idea of how passwords are stored. First, when you type it in, it is encrypted into something long. Method 1: Copy SAM & SYSTEM Files with Admin Rights. If you can log into Windows as a user with administrative rights, you can easily dump the SAM and SYSTEM registry hives using the Command Prompt. Just open the Command Prompt as Administrator, and then run the following commands: reg save HKLM SAM C: sam reg save HKLM SYSTEM C: system. Mar 18, 2002 Let me start with what this is all about: SAM Files & NT Password Hashes. NT Password Hashes - When you type your password into a Windows NT, 2000, or XP login Windows encrypts your password using an encryption scheme that turns your password into something that looks like this. Step 1: Extract Hashes from Windows Security Account Manager (SAM) is a database file in Windows 10/8/7/XP that stores user passwords in encrypted form, which could be located in the following directory: C: Windows system32 config The first thing we need to do is grab the password hashes from the SAM file.
VaultPasswordView is a simple tool for Windows 10/8/7 that decrypts and displays the passwords and other data stored inside 'Windows Vault'.You can use it to decrypt the Windows Vault data of your currently running system, as well as the Windows Vault data stored on external hard drive.Versions History
- Version 1.10:
- Added new option: 'Decrypt vault files of all logged-in users'. This new option allows you to decrypt the Windows Vault files of non-administrator user without typing the password, as long as the user is already logged into your system.
- Version 1.08:
- Multiple users reported about 'Invalid key file inside the Protect folder' error. The error message was incorrect and now it's displayed as 'Invalid key in policy file'.Also, added debug information to this error message in order to find out the cause of this error.
- Version 1.07:
- Fixed bug: When VaultPasswordView failed to find any data inside Windows Vault, it displayed the wrong message - 'Cannot find the Policy.vpol file inside the vault folder' instead of 'Cannot find any .vcrd file inside the vault folder'.
- Version 1.06:
- Fixed the lower pane to switch focus when pressing tab key.
- Version 1.05:
- VaultPasswordView now allows you to decrypt the data stored inside Windows Vault of the current user without supplying the login password and other information. This feature requires elevation (Run As Administrator) and on 64-bit systems you must use the 64-bit version of VaultPasswordView.
- Version 1.01:
- Fixed bug: VaultPasswordView detected the user profile folder incorrectly.
- Version 1.00 - First release.
System Requirements
- This utility works on any version of Windows, starting from Windows 7 and up to Windows 10. Both 32-bit and 64-bit systems are supported. Be aware that this tool is not very useful on Windows 7, simplybecause Microsoft started to use the Windows vault for storing IE and Windows mail passwords only from Windows 8.
- You can also use this tool on Windows XP with SP3 for decrypting the Windows Vault of external drive with Windows 10/8/7.
Decrypt Sam File Windows 7 Gratis
Passwords And Data Stored by Windows Vault
- Passwords of Internet Explorer 10.0/11.0 and Microsoft Edge running under Windows 8 or later. (Be aware that IE10/IE11 under Windows 7 doesn't use the Windows Vault to store passwords).
- Login Information of Windows Mail application (Windows 8 or later).
Windows Vault Location
Windows vault files are stored in the following folders:- C:Users[User Profile]AppDataLocalMicrosoftVault
- C:ProgramDataMicrosoftVault
- C:Windowssystem32configsystemprofileAppDataLocalMicrosoftVault
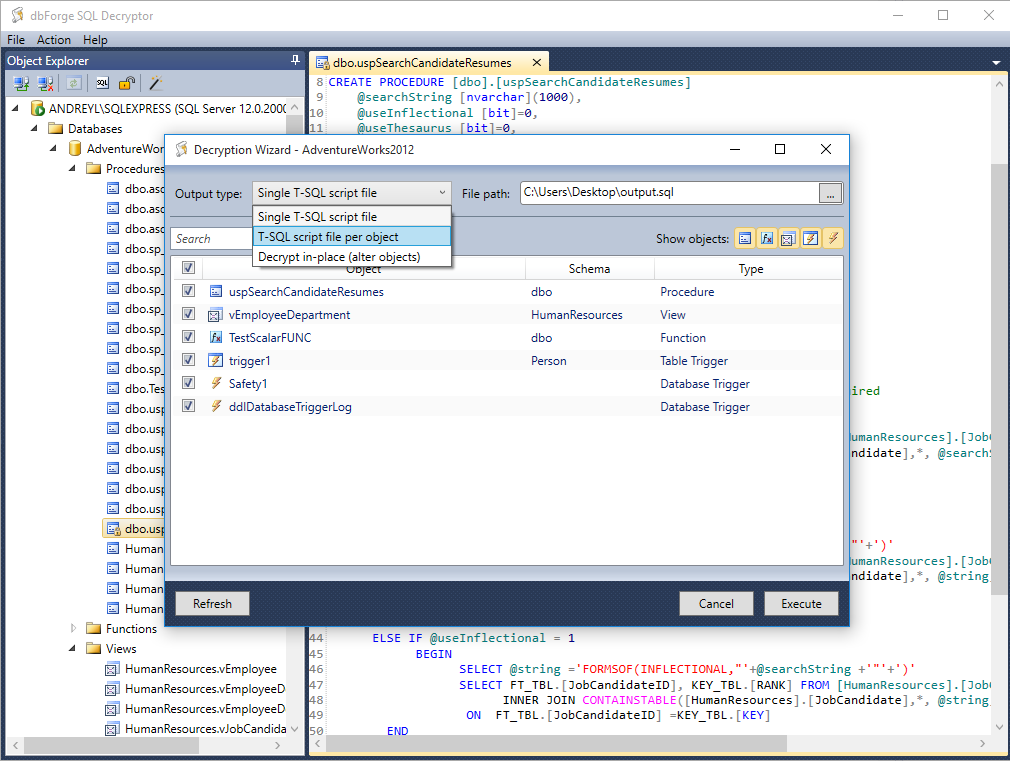 Inside these vault folders, there is Policy.vpol filename that contains the encryption key.The encryption key is used to decrypt the .vcrd files in the same vault folder.
Inside these vault folders, there is Policy.vpol filename that contains the encryption key.The encryption key is used to decrypt the .vcrd files in the same vault folder.Notice For Windows 7 Users
The term 'Windows Vault' is somewhat confusing because the passwords displayed by Windows 7 as Windows Vault are actually stored inside Credentials files.So if you have Windows 7 and you want to recover the passwords listed in the 'Windows Vault' window you should actually use the following tools:Network Password Recovery orCredentialsFileViewStart Using VaultPasswordView
VaultPasswordView doesn't require any installation process or additional DLL files.In order to start using it, simply run the executable file - VaultPasswordView.exeAfter running VaultPasswordView, the 'Vault Decryption Options' window is displayed. VaultPasswordView automatically fills the correct folders of your current running system and current logged-on user.The only field you have to fill by yourself is the 'Windows Login Password', the login password is needed in order to decrypt the Windows vault files.
You can also decrypt the data of Windows Vault of the current logged-on user without providing the login password if you choose the 'Decrypt vault files of the current user' option in the top combo-box. This feature requires elevation (Run As Administrator) and also you must use the 64-bit build of VaultPasswordView if you have 64-bit version of Windows.
If you have multiple logged-in users (For example: non-administrator user that owns the vault data you want to decrypt, and Administrator user that you use for the elevation of VaultPasswordView), you should choose the 'Decrypt vault files of all logged-in users' option.
If you want to decrypt the Windows vault files of external drive, you can manually fill the correct folders on your external drive, or alternatively you canchoose the root folder of your external drive and then click the 'Automatic Fill' button.
After clicking the 'Ok' button of the 'Vault Decryption Options' window, VaultPasswordView scans the files inside the vault folders, decrypts them and thendisplays the result in the main window. The upper pane of the main window displays the list of all decrypted .vcrd files.When selecting an item in the upper pane, the lower pane displays the entire decrypted data in Hex-Dump format.If the decrypted data contains a password or other text, this text is also displayed in the 'Item Value' column on the upper pane.
Run As Administrator
By default, VaultPasswordView doesn't request elevation (Run As Administrator) when running it.However, if you have vault files encrypted with a system key - you have to run VaultPasswordView as Administrator in order to decrypt these vault files.You can run VaultPasswordView as administrator by pressing Ctrl+F11.Translating VaultPasswordView to other languages
In order to translate VaultPasswordView to other language, follow the instructions below:- Run VaultPasswordView with /savelangfile parameter:
VaultPasswordView.exe /savelangfile
A file named VaultPasswordView_lng.ini will be created in the folder of VaultPasswordView utility. - Open the created language file in Notepad or in any other text editor.
- Translate all string entries to the desired language.Optionally, you can also add your name and/or a link to your Web site. (TranslatorName and TranslatorURL values) If you add this information, it'll be used in the 'About' window.
- After you finish the translation, Run VaultPasswordView, and all translated strings will be loaded from the language file.
If you want to run VaultPasswordView without the translation, simply rename the language file, or move it to another folder.
License
This utility is released as freeware. You are allowed to freely distribute this utility via floppy disk, CD-ROM, Internet, or in any other way, as long as you don't charge anything for this and you don'tsell it or distribute it as a part of commercial product. If you distribute this utility, you must include all files inthe distribution package, without any modification !Disclaimer
The software is provided 'AS IS' without any warranty, either expressed or implied,including, but not limited to, the implied warranties of merchantability and fitnessfor a particular purpose. The author will not be liable for any special, incidental,consequential or indirect damages due to loss of data or any other reason.Feedback
Windows Sam File Location
If you have any problem, suggestion, comment, or you found a bug in my utility, you can send a message to nirsofer@yahoo.com| Download VaultPasswordView (32-bit) |
| Download VaultPasswordView (64-bit) |
VaultPasswordView is also available in other languages. In order to change the language of VaultPasswordView, download the appropriate language zip file, extract the 'vaultpasswordview_lng.ini', and put it in the same folder that you Installed VaultPasswordView utility.
| Language | Translated By | Date | Version |
|---|---|---|---|
| Arabic | Ammar Kurd | 07/02/2019 | 1.08 |
| Brazilian Portuguese | igorruckert | 25/09/2016 | 1.00 |
| Dutch | Jan Verheijen | 08/08/2020 | 1.10 |
| French | Largo | 30/09/2018 | 1.08 |
| German | «Latino» auf WinTotal | 06/08/2020 | 1.10 |
| Greek | geogeo.gr | 28/07/2017 | 1.06 |
| Italian | Andrea Carli | 31/12/2020 | 1.10 |
| Simplified Chinese | DickMoore | 24/05/2020 | 1.08 |
| Slovak | František Fico | 17/08/2020 | 1.10 |
| Spanish | Ricardo A. Rivas | 06/08/2020 | 1.10 |
| Traditional Chinese | Danfong Hsieh | 07/08/2020 | 1.10 |
| Turkish | Cemil Kaynar | 26/05/2017 | 1.06 |
Category: «General»
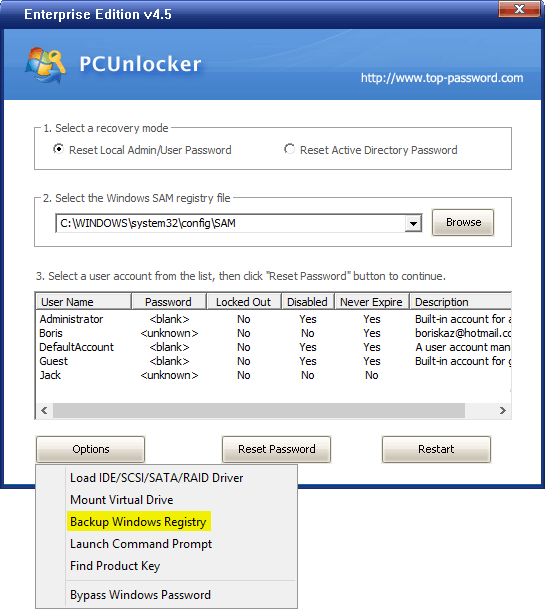
Some 22 years ago, Microsoft made an attempt to make Windows more secure by adding an extra layer of protection. The SAM Lock Tool, commonly known as SYSKEY (the name of its executable file), was used to encrypt the content of the Windows Security Account Manager (SAM) database. The encryption was using a 128-bit RC4 encryption key.
The user had an option to specify a password that would protect authentication credentials of Windows accounts stored in the SAM database. If SYSKEY password was set, Windows would ask for this password during startup before displaying the login and password prompt.
While SYSKEY was not using the strongest encryption, attacking (brute-forcing or resetting) the user’s Windows login and password would not be possible without first decrypting the SAM database. As a result, a SYSKEY password would require the attacker to brute-force or reset SYSKEY protection prior to accessing the system’s Windows accounts. More importantly, an unknown SYSKEY password would prevent the user’s system from fully booting. This fact was widely exploited by ransomware and commonly abused by “tech support” scammers who locked victims out of their own computers via fake “tech support” calls.
Due to SAM database encryption, reinstalling or repairing Windows would not solve the issue unless the user had access to a recent backup or a System Restore Point. For this reason, Microsoft removed the ability to set SYSKEY passwords in Windows 10 (release 1709) and Windows Server 2016 (release 1709), steering users towards the much more secure BitLocker encryption instead. However, older systems are still susceptible to SYSKEY ransomware attacks.
Decrypt Sam File Windows 7 64-bit
Since SYSKEY protection is fairly old by hi-tech standards, it is no longer secure (it never been in the first place). Victims of SYSKEY ransomware or “tech support” scammers can now restore their systems by recovering or resetting SYSKEY password. Elcomsoft System Recovery has the ability to discover or reset SYSKEY passwords in order to restore the system’s normal boot operation. This is also the first time ever we’re publishing screen shots of the Elcomsoft System Recovery user interface.
Removing SYSKEY Password
SYSKEY encryption is a relatively little known feature that was actively exploited by “tech support” scammers and ransomware. Once a SYSTEM password is activated, the entire SAM registry hive is encrypted. This makes it difficult to restore Windows to working condition, especially if the scammer has also removed all System Restore points. Victims of this scam will see the following message when they attempt to start their computer:
“This computer is configured to require a password in order to start up.”
Elcomsoft System Recovery can attempt to automatically reset SYSKEY protection. A straightforward removal of SYSKEY password bears the risk of breaking the Windows boot process. For this reason, Elcomsoft System Recovery performs a number of safety checks to determine whether resetting a SYSKEY password of the particular system may cause issues.
Note: instructions below assume that you already created a bootable media containing Elcomsoft System Recovery 5.40 or newer.
In order to remove an unknown SYSKEY password, do the following.
Decrypt Sam File Windows 7 64 Bit Mien Phi
- Boot your computer to bootable storage media with Elcomsoft System Recovery. Depending on your computer’s motherboard manufacturer, you may need to press Del, F8, F11, F12 or another key to invoke a special menu to temporarily override boot order or to enter UEFI/BIOS setup.
- In Elcomsoft System Recovery, specify the disk or partition where Windows is installed, then click Next.
- The ability to remove SYSKEY passwords is located under Miscellaneous.
- Choose SYSKEY.
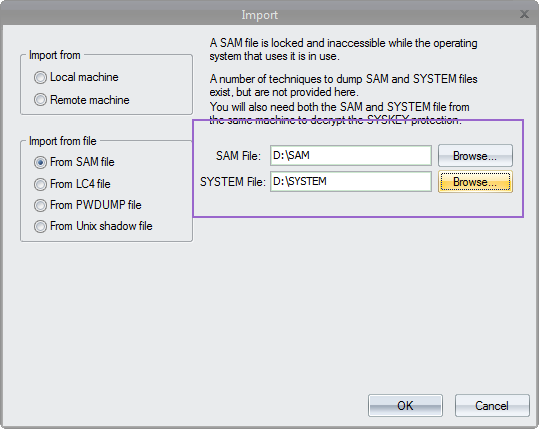
- Select whether ESR should automatically search for the SAM database or specify its location.
- The tool will perform the necessary safety checks and warn you if a potential issue is detected. To just reset the password, leave the “Search…” option blank. Click “Reset SYSKEY” to finish.
- Finally, reboot your computer. Windows should start normally.
If a potential issue is discovered, you will see the following warning:
If you proceed, you will lose access to DPAPI encrypted data (EFS-encrypted files and folders). In addition, we recommend that you make backup copies of SAM, SYSTEM and SECURITY registry hives (this must be done manually).
Sam File Reader
Discovering SYSKEY Password
Sam File Location
Resetting the SYSKEY password may or may not work depending on configuration of the particular system. Recovering the SYSKEY password is a significantly safer operation that does not have the potential negative impact of simply resetting the password. Elcomsoft System Recovery can automatically check your computer to look up for cached SYSKEY passwords throughout the system. The tool will analyze various registry keys, temporary files and databases to look up for a cached copy of SYSKEY password. If this is successful, SYSKEY protection can be removed instantly and risk-free.
In order to look up for SYSKEY password, do the following:
- Boot your computer to bootable storage media with Elcomsoft System Recovery. Depending on your computer’s motherboard manufacturer, you may need to press Del, F8, F11, F12 or another key to invoke a special menu to temporarily override boot order or to enter UEFI/BIOS setup.
- Follow steps 2 through 6 in Elcomsoft System Recovery. However, this time make sure the “Search for SYSKEY plain text password” option is selected.
- You will have the choice between a fast or thorough scan. Tap Recover SYSKEY to continue. The tool will attempt to locate the SYSKEY password on your computer.
- Take a note of the discovered SYSKEY password and reboot your computer. Enter the discovered SYSKEY password when prompted.